Microsoft Azure, one of the leading cloud platforms, offers individual customers, startups and large enterprises to manage and deploy applications and services. It also enables enterprises to scale out, scale up and scale down as per their business requirements. Azure helps enterprises to control their CAPEX and OPEX and allows building and deploying long term and sustainable workloads.
Owing to the Azure offerings, it appears that Azure cloud services are growing tremendously. The Azure platform is getting more matured and providing better support for security, business analytics, Hadoop and other value add services. Azure backs a wide range of programming environments including ASP.NET, PHP and Node.js covering best of both worlds Microsoft and Open Source.Azure Cloud Trend:

The network of datacenters managed by Microsoft is considered as backbone for Azure Platform. The presence of Azure is in 140 countries by supporting 10 languages and 24 currencies backed by the global datacenter infrastructure. Azure includes latest infrastructure technologies having a high focus on consistency, operational excellence, cost-effectiveness, environmental sustainability and providing an excellent online experience to customers and partners globally.
Though many businesses are opting and migrating towards Azure cloud services to get things done at level of efficiency, the notion of cloud adoption still persist fears and concerns mostly due to privacy of their data and their customer data, security of the applications, data and compliance.
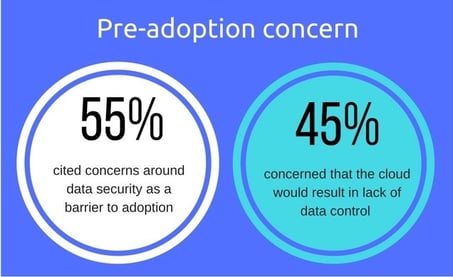
Below are some common myths and concerns due to which businesses are skeptical about adopting Azure Platform.
- Businesses / Enterprises who are still doing business on-premises -
Customers spend lot of time, money and efforts to maintain security of data, applications and infrastructure. Lots of businesses are under an impression that if they move their data to Azure, their data privacy is compromised, as their applications, data and privacy will be controlled by Azure service provider. This is the foremost reason why most of the CIOs and decision makers consider data and privacy issue as a roadblock in adopting Azure including other compliance concerns. - Familiar with Azure features, lack of awareness about security, data privacy and compliance -
There is lack of awareness within the businesses when it comes to shared responsibility while managing the security strategy with the provider. The cloud provider is equally responsible for the physical aspects of the cloud IT Infrastructure and the software it provides whereas the businesses are responsible for its own data. The cloud service providers alone cannot protect the users, service offerings and applications from vulnerability. - Perception -
Businesses believe that the data stored on Azure cloud is prone to threats, given that it is being maintained and managed by Microsoft. They also consider that once the data has been migrated to cloud they lose the control over the data. But this may not be the case. The primary function of the Microsoft is watching over the network and maintaining the data at the data center which can free lots of resources in an organization to focus mainly on the business outcomes.
If you are still not sure about migrating your data to Azure cloud, here are some common answers for Azure concerns.
- Does Microsoft has any security centers of excellence for Azure Platform?
The security, privacy and compliance of the Azure starts with a trustworthy technology foundation. Microsoft follows steps to create and implement security oriented software development, operational and threat mitigation practices. Microsoft involves industry leading efforts for security through creation of centers of excellence including Microsoft Digital Crimes Unit, Microsoft Security Response Center and Microsoft Malware Protection Center.
- What is Assume breach strategy and how it works?
The Assume breach strategy allows Microsoft to harden its cloud services and stay ahead of the emerging threats. A dedicated ‘red team’ of security experts encourage real-world attacks at the networks, platform and applications questioning the ability of Microsoft Azure to detect and protect against security breaches.
- Does Azure has an incident response service?
Azure consists of a global 24/7 incident response service that works to reduce the effects of the attack and malicious activities. The incident response team follows a standard procedure for incident management, communication and recovery. - Is Infrastructure protection provided by Azure?
The infrastructure of Azure consists of hardware, software, administrative and operation staff. It also includes physical data centers. Azure can identify security risks within its infrastructure with continuous intrusion detection and prevention systems, denial of service attack prevention, regular penetration testing and forensic tools. With the help of Azure, customers can decrease the requirements to invest into these capabilities on their own and benefit from the same. - Is 24-hour monitored physical security offered by Azure?
The datacenters are physically constructed and monitored 24 hours a day to protect data and services from unauthorized access. Centralized monitoring, correlation and analysis systems manage huge volumes of data generated by devices. Timely alerts and continuous visibility is provided to the teams monitoring the Azure environment. - Is patch management available in Azure?
Security patches protect the systems from vulnerabilities. The integrated deployment systems manage the distribution and installation of the security updates by Azure. - Does Microsoft provide anti-virus or anti-malware protection for virtual machines?
Cloud services have a built-in service anti-malware solutions and can be enabled for virtual machines also. Enabling the anti-malware solution for VMs can identify and remove virus, spyware and other malicious software by providing real-time protection. Customers can also run anti-malware solution from partners on their VMs. - How frequently Microsoft performs penetration testing?
Regular penetration testing is performed by Microsoft in order to improve Azure security control and processes. Customers can also carry out authorized penetration testing for the applications hosted on Azure. - Is network protection proffered by Microsoft?
Microsoft has made necessary infrastructure available to securely connect VMs with one another and to connect on-premises data centers with Azure VMs. Azure can block unauthorized traffic using technologies like firewalls, partitioned LAN physical separation of back-end servers from public-facing interfaces. - Is data protection available in Azure?
Technological safeguards such as encrypted communications and operation processes aids in securing the data for the customers. Customers also have the flexibility to implement additional encryption and manage their own keys.
Although in above section we have seen that how Microsoft as a service provider and Azure as a platform ensures security, privacy of your data and applications. You as an individual customer, business or enterprise also have equal responsibilities to ensure security of your applications and data and privacy. Concept of “Shared Responsibilities” plays a vital role here.
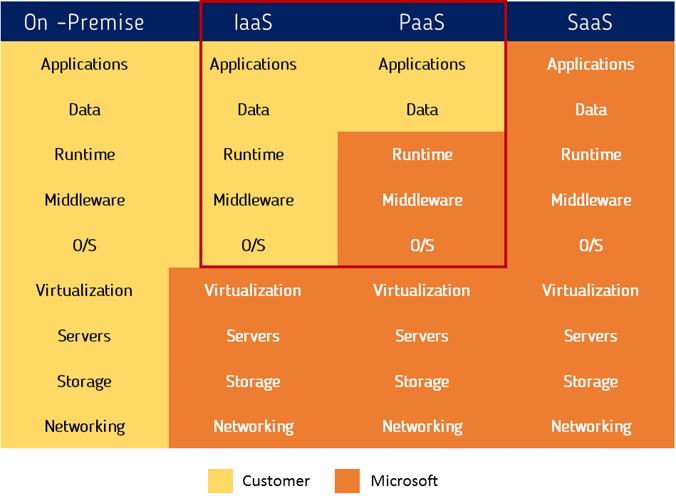
As a customer, one needs to ensure following things -
- Understand the offerings of the Azure platform well (Refer : http://blog.e-zest.net/here-are-10-most-common-mistakes-while-managing-azure-cloud)
- Understand best practices of Azure while creating and maintaining Azure components and services
- Ensure you follow best practices for application development
- Ensure you follow best practices for application security (Appropriate Authentication/Authorization mechanism, user preferences and encryption etc.)
- Define your classified data and then align security and privacy of the data with available Azure services.
Summary -
- Your data remains with you and you have full control
- Microsoft neither have any visibility of your actual data nor they can access your data
- For compliance, Microsoft ensures to follow set of international and industry-specific compliance standards, such as ISO 27001, HIPAA, FedRAMP, SOC 1 and SOC 2 along with country specific standards like UK G-Cloud and Singapore MTCS.
If you are able to clarify the myths about the cloud which tend to restrict the perception of Azure cloud ability, you can get a clear picture on how cloud can be the solution to improve the way an organization operates.



.jpg)
.jpg)