OWASP ZAP is an open-source web security testing tool, used for detecting vulnerabilities in web applications.
ZAP provides you with configured automated scanners as well as a set of tools that allows you to detect vulnerabilities and threats manually. It is designed for people with a wide range of security expertise and is in a way ideal for developers and functional testers who are new to penetration testing and is also a useful to an experienced pen tester’s skillset.
This is a cross-platform tool written in Java, available in all of the operating systems including Microsoft Windows, Linux and Mac OS X.
OWASP ZAP 2.5.0 has four modes:
- Safe mode – This mode doesn’t allow you to do anything that is potentially dangerous.
- Protected mode – This mode allows you simulate potentially dangerous vulnerabilities. User can only perform harmful actions on URLs which are mentioned in the scope.
- Standard mode – In this mode user can do anything that is relevant.
- ATTACK mode - New nodes in scope are actively scanned as soon as they are discovered.
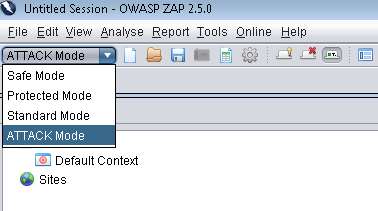
It is strongly recommended that you use the ‘Protected mode’ to ensure that you only attack sites that you mean to.
The mode can be changed via the toolbar and is persisted between sessions.
Things that will not be possible in either ‘Safe mode’ or ‘Protected mode’ when not acting on URLs in the Scope:
- Spider - crawling
- Active Scanning
- Fuzzing
- Force Browsing
- Breaking (intercepting)
- Resending requests
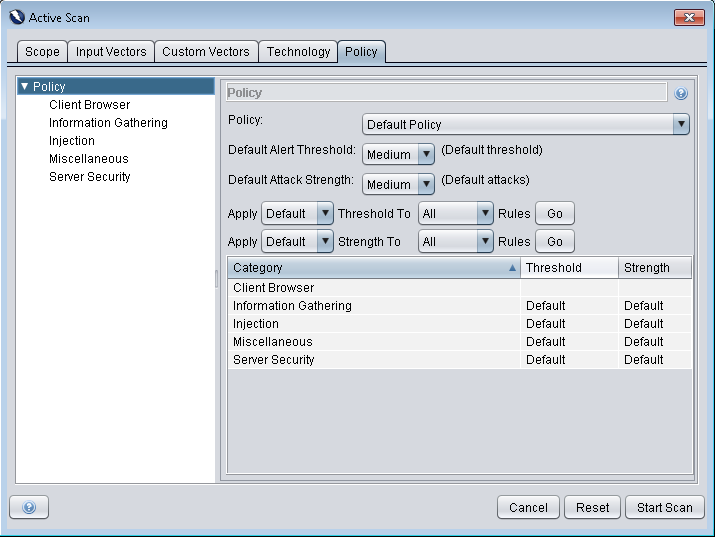
We can define the scan policy to be used for the attack mode in the Options Active Scan screen.
Reference: https://www.owasp.org