Since we have explored the depths of GDPR in my previous blogs, we are now equipped with the required knowledge, which would help us at looking at different scenarios for application of this new policy. Reflecting on these scenarios would aid organizations to assess their capabilities to become GDPR compliant.But before we proceed further, I would like to add one more dimension in the DPIA, a concept I had outlined in my last blog. You may recall the part where I discuss the classification of the private data using the technique of ‘CIA’ (Confidentiality, Integrity, and Availability). For privacy of information, I would like to introduce another parameter- sensitivity-which will provide us with better input for information classification and identify risks associated with this information.
With that being said, it is time to delve into the main motive for this article. I will attempt to explain a typical ‘HR and Talent Acquisition (TA) function’ scenario in an organization in the context of GDPR. In this context, the organization is the controller gathering information about the data subject.
Scenario 1- HR and TA functions in the organization
To avoid having complications of implementing two systems for data privacy, even though I have described this scenario in the context of EU citizens, the system should be developed to cater to the protection of private information of people irrespective of their country of citizenship. Perhaps other nation-states may soon follow the lead of their European counterparts, and so it is always better to prevent than cure the issues that might pop up as a result.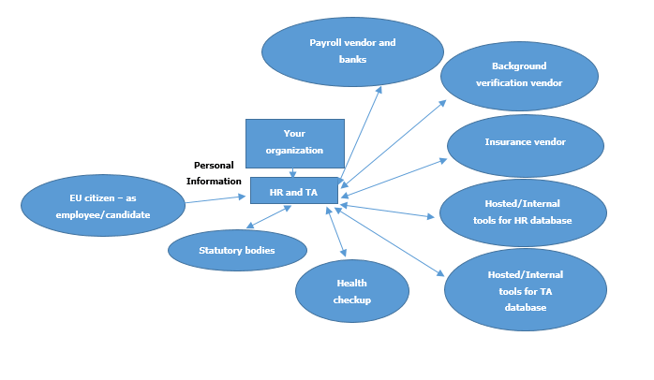 If we look at the above figure, we can trace the flow of data from the EU citizen (Data Subject - DS) in the HR function. The details are as follows:
If we look at the above figure, we can trace the flow of data from the EU citizen (Data Subject - DS) in the HR function. The details are as follows:
- Information about Data Subject gets gathered at two stages:
- When a DS applies for the job, he or she has to fill in his/ her
- Name
- Contact details – Telephone number, email ID, LinkedIn profile URL
- Address
- DOB
- Educational qualifications
- Passport/VISA details
- Work history
- Sex
- Marital status
- Contact details of references
- Past and expected salary
- Miscellaneous data relevant to the job being applied for
- When the DS gets employed in the organization and his/her information enters the HR database
- All this information is entered in the TA tool, which can be internal or hosted. Some organizations use Excel sheets that are most often than not saved on individual computers.
- These profiles are shared with internal and/or external people including clients conducting interviews.
- Their evaluation remarks are recorded.
- Sometimes their information is shared with background check vendors.
- Offers are made and once accepted, appointment letters are sent with compensation details.
- In some organizations, these profiles are printed and those hard copies are floating in the organization. There is no method to control distribution, to return collection and to dispose of these profiles.
Once the job applicants become employees, HR function comes into the picture. (Some organizations have HR and TA as the same function). The HR function in the organization generally gathers and/or generates additional information from the employees:
- Personal identification information – information of close relatives, their contact details
- Health information – blood group, health records
- Compensation information – This is generally processed through a third party vendor
- Financial details - Bank name, account number, loan status
- Taxation details – savings, investment portfolios
HR has different internal and/or hosted tools or they may choose to use Excel to process and store the information. Does your HR inform the data subjects what information is needed, why it is needed, how we plan to use it, where it will be stored, and for how long it intends to retain the data?
Should a data breach be identified, it becomes mandatory for the organization, serving in the controller role, to inform data subjects and the DPA. This intimation must be provided within 72 hours from the time it is noticed. You may then act to control the damage and ensure it is not duplicated in the future.
If data subject asks for amendments or deletion of his/her information, acknowledge this request, identify and locate where all this information is stored, and make necessary amends to it. This has to be taken care of within 30 calendar days from the date you will have received the request. If the information cannot be deleted for statutory reasons, inform the data subject accordingly.
Situations might arise when a data subject asks to view and/or port his/her information to another employer. In this case, you must provide this information in machine-readable format. Identify the word ‘data subject’ in the above 3 paragraphs as ‘data subject or his/her legal representative’.
When we consider this, we can clearly recognize the scope of this information flow and its exposure within and outside of the organization. As you can tell, it may become really challenging to protect this information. However, when one prepares an inventory of privacy information and performs DPIA, we can gain clarity on the source, journey, and destination of this information. By being mindful of who has access to the data and what processes are performed on this data and for how long, we are ensuring compliance to what could make or break your current and future deals with your EU clientele. You should also be wary of the risks involved in handling the plethora of information you collect and process and spell out a process to protect this data.
The GDPR unleashes the following golden rule: collect, retain and provide access to data that is required. It is important to carry out a VAPT (Vulnerability Assessment and Penetration Test) for the internal and external applications, IP addresses, tools used, and conduct security audits of the vendors. Check if you need to mask, anonymize, pseudonymize or encrypt the data. Check also the effectiveness of the policies you institutionalize. If you do not have data stored centrally, you have a very big challenge to address. Procrastination then may not be an option.
You will also have to check the existence of a privacy statement declaring everything we have just spelled out and also to seek the consent of the data subject if you plan to use their information for purposes other than those mentioned in the privacy statement. It is important to provide links to the privacy statement and consent form on the
- Career page of your website where prospective candidates are submitting their profiles, and
- Intranet for the employees of the organization
I believe I have provided enough wind to mobilize your HR and TA functions. Feel free to tailor these requirements based on the scope of the HR and TA activities of your organization. Let us interact next week with a different scenario.






