In digital world we have to transfer messages every now and then. The security of the message is important while we transfer such messages to people around or spread across world. Encryption and decryption plays an important role in the complete process. Another important aspect of this is sharing this securely without storing a passkey.
Let’s break this in two parts – encryption process and decryption process.
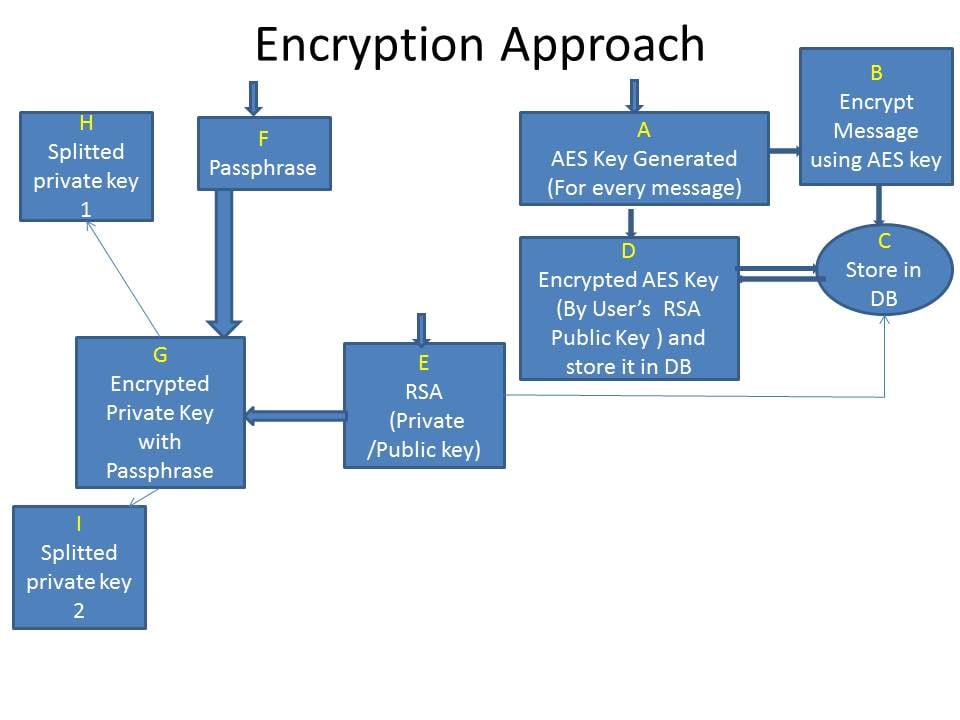
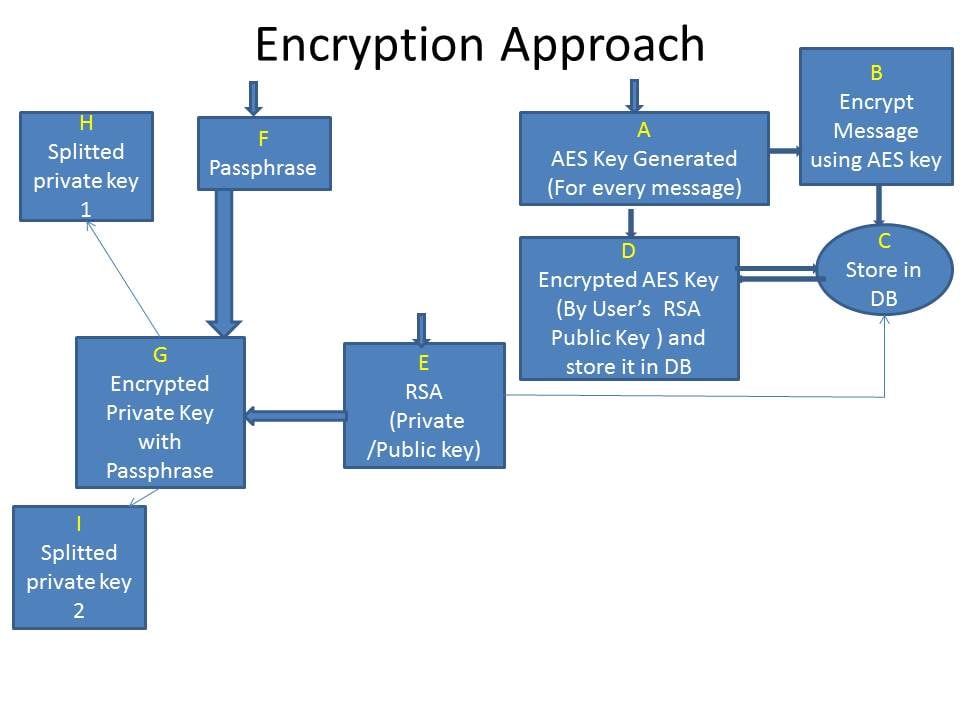
Encryption Process (Part A)
For Data Encryption & AES (Advanced Encryption Standard) Key Encryption
Step 1: Generate AES Key on run time for every message
Step 2: Encrypt message through AES Key and stored message into database
Step 3: Encrypt AES Key using Sender’s RSA Public Key and store the encrypted Key into the database
Step 4: Encrypt the AES Key using assigned user’s (with whom the message will be shared) RSA Public Key.
Encryption Process (Part B)
Private/Public Key using RSA Algorithm
Step 1: Generate Public and Private Keys for every receivers
Step 2: Store Public Key into the database
Step 3: Encrypt the Private Key using user’s Passkey (which is input by user) and split the encrypted Key into two parts and store one part in a vault (Say Pk1) and store second part in another vault (Say pk2).
Encryption Process (Pictorial representation)
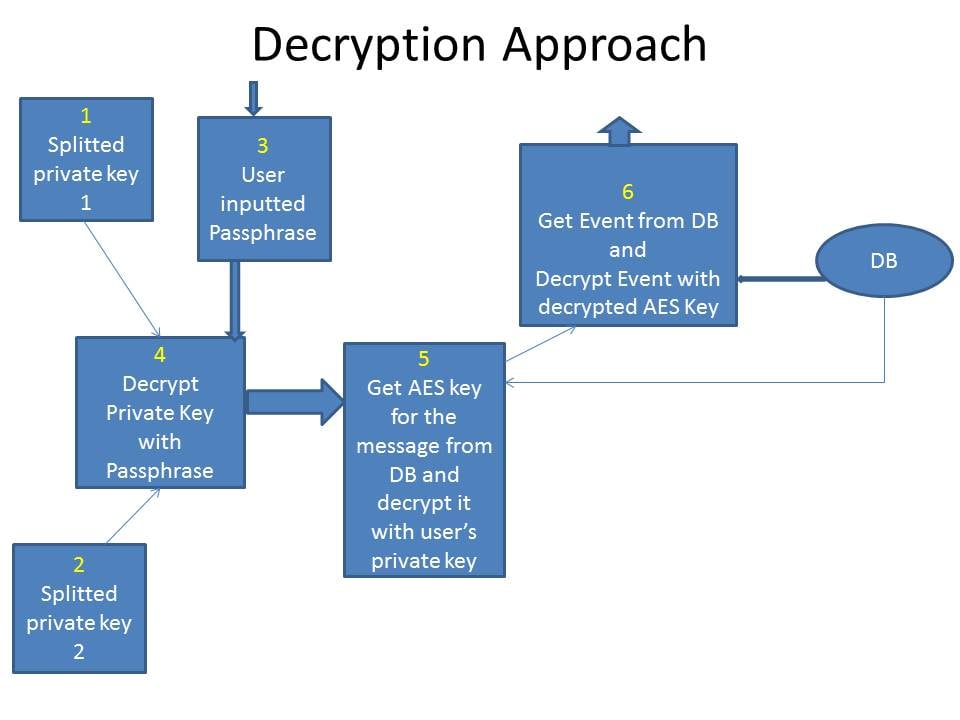
Decryption Process
Step 1: Fetch the encrypted Private Key of the user from two different vaults (Say pk1 and pk2) say EPK
Step 2: Decrypt encrypted Private Key (EPK) using logged in user’s Passkey say PK
Step 3: Decrypt AES encrypted Key (stored in the database for the specific message for the specific user) using user’s Private Key (PK) say AK.
Step 4: Decrypt the message from decrypted AES Key (AK)
Decryption Process (Pictorial representation)