“App Transport Security has blocked a cleartext HTTP (http://) resource load since it is insecure. Temporary exceptions can be configured via your app's Info.plist file. “
Have you ever encountered this message? Think of the times when you were debugging or when your app’s network connections to server failed when you linked your app against iOS 9.0 or OSX 10.11 SDK. If yes, it is high time to learn more about Apple’s latest introduction to its SDKs - App Transport Security (ATS)
What is App Transport Security?
From iOS 9.0 and OS X v10.11 onwards, a new security feature called App Transport Security (ATS) was introduced to apps and enabled by default. It enforces the privacy and data integrity of connections between an application and web services by applying additional compulsory security requirements for HTTP-based network requests. With ATS enabled, HTTP connections must use HTTPS connections. If apps try to connect with an insecure HTTP connection, it will fail. Additionally, HTTPS connections should also satisfy some requirements which will be explained later in the blog.
ATS requires minimum Transport Layer Security (TLS) protocol version 1.2 NSURLSession class and all APIs that use this class enforce ATS. ATS is enabled by default made when you link your app against the iOS 9.0 SDK or OS X v10.11 SDK and onwards. If you are using an old NSURLConnection class and link it against iOS 9.0 /OS X 10.11 SDK, it will also enforce ATS.
ATS is only available on iOS 9.0 or OSX 10.11 SDK and later. For older versions, it is not required.
Why is it used?
HTTP connection requests transmit data in cleartext Format (data without cryptographic protection and easily understandable). This poses a great security threat to the data. For Apple, security of their app’s customers is top priority. With this move, they are trying to make sure that the data of their customers remains safe and secure, even when it is not sensitive. With ATS, Apple has practically ensured safety of customer’s data by incorporating the best security practices. With the help of ATS, Apple enforces users to send data over a secure network usi9ng HTTPS connections.
NSAppTransportSecurity Key
This key is used to describe how app network connections will behave when connected to web services or servers. If an app uses a secure network connection, then there is no need for NSAppTransportSecurity key irrespective of the SDK versions in use. If the app links to older versions, there is no need to use NSAPPTransportSecurity key. If the app is linked with iOS 9.0 or OSX10.11 SDK, then the connections are not fully secured and must include NSAppTransportSecurity key which is nothing but a dictionary with collections of several other keys.
NSAppTransportSecurity Dictionary Structure
NSAppTransportSecurity : <Dictionary>
{
NSExceptionDomains
{
<domain-name-string> :
{
NSIncludesSubdomains : <Boolean Value>
// These are keys which are set with appropriate values to describe app’s network behavior whose security attributes can be controlled for its behavior
NSExceptionAllowsInsecureHTTPLoads : <Boolean Value>
NSExceptionRequiresForwardSecrecy : <Boolean Value>
NSExceptionMinimumTLSVersion : <String Value>
// These are keys which are set with appropriate values to describe app’s network behavior whose security attributes cannot be controlled for its behavior
NSThirdPartyExceptionAllowsInsecureHTTPLoads : <Boolean Value>
NSThirdPartyExceptionRequiresForwardSecrecy : <Boolean Value>
NSThirdPartyExceptionMinimumTLSVersion : <String Value>
}
}
NSAllowsArbitraryLoads : <Boolean Value>
}
Different scenarios
Here are some different scenarios for network connections which behave in an appropriate environment when ATS is enabled:
- HTTPS Only
If your app is only connected with servers that support HTTPS, you do not need to make any change in the app unless its supports TLS 1.2 and expects the domain to use ciphers that will support forward secrecy. The certificate also needs to meet the following requirements imposed by ATS:
- The server certificate requirements:
- Server certificate should be Issued by a Certificate Authority (CA) whose root certificate is incorporated in the operating system
- Should be issued by a trusted root CA and installed by the user or a system administrator
- The minimum Transport Layer Security version must be TLS 1.2
- TLS connection cipher must support forward secrecy (FS) and one of the following:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- The leaf server certificate must be signed with one of the following types of keys:
- Rivest-Shamir-Adleman (RSA) key with a length of at least 2048 bits
- Elliptic-Curve Cryptography (ECC) key with a size of at least 256 bits
In addition, the leaf server certificate hashing algorithm must be SHA -256
B. Domains that not do not work with ATSDomains that do not work with ATS specify exceptions where ATS should not be used. Use NSExceptionDomains to override ATS default settings
Set the following keys:
NSIncludesSubdomains:TRUE // Disable ATS for subdomains as well
NSExceptionAllowsInsecureHTTPLoads :TRUE
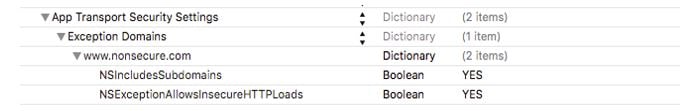
C. Some domains that work with ATS and rest do not
Sometimes you want certain URLs to be secure in your Application e.g Login Calls while others need not be secure
To achieve that, set the following Keys
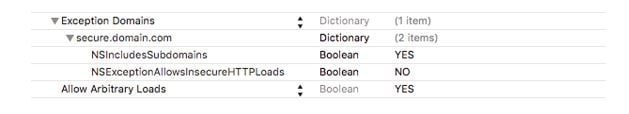 D. Some domains that work with ATS but are not supported fully
D. Some domains that work with ATS but are not supported fully
When a URL wants ATS to be enables but doesn’t support it fully (less-secure HTTPS connection), you can enable ATS and add the following exceptions flag
NSExceptionRequiresForwardSecrecy & NSExceptionMinimumTLSVersion as required
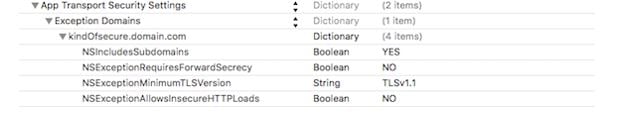
E. For Domains that do not work with ATS
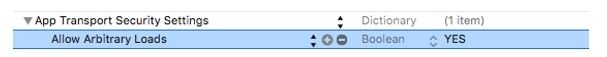
Ideally NSAllowsArbitraryLoads must be set at NO because it disallows all insecure connections and adds domains in exception list to allow connection without Https using scenario B above.
The Specification for domain name key for an exception dictionary:
- Must be lowercased to work correctly
- Must not include a port number
- Must not be a numerical IP address (but rather a string)
- Must not end with a trailing dot.
References:

.jpg)
