As a professional Marketing speaker, Bryan Eisenberg has said, “Facts tell, but stories sell.” Let us understand the significance of information security as work culture through this story.
Story:
“Hey Hi…” Re(Reactive)-Ramesh called his friend “Pro(Proactive)-Paresh” in the cafeteria of the organization.
“Hi! How are you, friend?” Pro-Paresh walked up to him.
“Busy?” Re-Ramesh asked him.
“Hmm. My new project has just started. I am analyzing the security requirements from the contract.” Pro-Paresh answered.
“I think you are overburdening yourself. In case there are any security requirements, then the client will share them with you.” Re-Ramesh said.
“I will take your leave now. A lot of work to do.” Pro-Paresh said and went back to work.
This was a conversation between two friends Pro-Paresh and Re-Ramesh who were working as Project Managers in an IT organization. Pro-Paresh was always proactive. His favorite quote was “If you fail to plan then you plan to fail.” He used to follow the organization’s policies and procedures while managing his projects. He was always prompt about the security of the client’s intellectual property in every form. On the other hand, the approach of Re-Ramesh was always reactive. He used to start working on the project without having a proper plan, policies, or procedures.
A few days later, both of them met again in the cafeteria. Re-Ramesh was sitting all alone at a table, quietly. He seemed dejected, disheartened, and desolate. Pro-Paresh went to him. “Hey, friend!!! All well?”
Re-Ramesh: “Nothing is well. Yesterday, a security incident happened in my project. The client was infuriated about it and he raised a complaint. I immediately called all the team members. We analyzed the situation and instantly corrected the web links. However, it DID NOT make the client happy.”
Pro-Paresh: “How did the incident happen?”
Re-Ramesh: “We missed one security requirement. Actually, the client was at fault. He did not mention it during the requirement collection meetings.”
Pro-Paresh: “Oh. Ok. However, I think that you could have avoided such an embarrassing situation by better planning.”
Re-Ramesh: “Was it possible? Haven’t you experienced a similar situation in your project ever?”
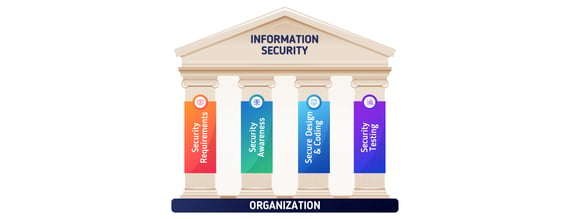
Pro-Paresh: “I have not come across such a situation yet. Let me share my knowledge with you. As far as I have learned from my projects, Information Security is based on 4 pillars; Security requirements understanding, security awareness, secure design and coding, and security testing.”
 Re-Ramesh: “This is interesting.”
Re-Ramesh: “This is interesting.”
Pro-Paresh: “The first pillar is security requirements understanding. Most of the time, the security requirements are mentioned in the project contract. Once we sign the contract, the organization is legally bound to fulfil those requirements. It is essential to understand those requirements. You may take the help of the legal team for the same. Additionally, during the requirement development phase, you may specifically discuss with the client and understand if there are any other security requirements.”
Re-Ramesh: “The client should share the security requirements with us before we ask him.”
Pro-Paresh: “You might be correct. However, clients might expect that a good organization like ours has information security as a best practice. Coming back to the security requirements, understand the organization’s security policies and practices as well. You may take the help of the Chief Information Security Officer to understand them. Lastly, we need to understand the client’s intellectual property as well. It might be in the form of documents, software licenses, previous applications, hardware devices, and developed code. Label the client’s intellectual property as applicable, and secure it physically and logically.”
Re-Ramesh: “Got it.”
Pro-Paresh: “Security awareness of the team is the second pillar". All the members of the project team must be aware of the security requirements that we discussed in the first point, including the client’s intellectual property. Ensure that each of them has undergone the information security awareness training. Check their awareness randomly. You may take help from the Chief Information Security Officer, Compliance team, and HR team for the same.”
Re-Ramesh: “Yes. I will surely do it.”
Pro-Paresh: “Now it’s the turn of the third pillar. It is secure design, and secure coding. Discuss with your Tech Lead and make sure that the security requirements are incorporated in application architecture. E.g. input validation, password and session management, SSL authentication, role-based authentication, encryption, etc. Discuss with the client and apply the principles such as separation of duties for access control. Maintain the list of access rights as well. You may also go through the secure design principles according to The Open Web Application Security Project (OWASP). (Darius Sveikauskas, 2021)
Apply technology-specific secure coding guidelines and get the security code reviews done at a defined frequency. Due to peer reviews, the project team members are also educated about the security requirements.”
Re-Ramesh: “This is really helpful. I am curious to know the fourth pillar.”
Pro-Paresh: “The fourth pillar is security testing. The Vulnerability Assessment and Penetration testing ensure that your web application is secure in the public domain. In addition to that, ensure that the test engineer uses the security test cases while testing the security requirements. The test data which is used for testing is also very important. Make sure that no real data is used for testing without the client’s approval. Secure the test data properly.”
Re-Ramesh: “Thanks, friend. Today you took off my blinkers. I have understood that information security is as important as delivering the solution on time. I will always keep the four information security pillars in mind. Now onwards, I will make information security as part of my work-culture.”
Pro-Paresh: “Great! If you do so, then you will contribute to the organization’s business objective of Client Satisfaction and your client will always be happy as Larry.”
Re-Ramesh went back to his work with a new zest, zeal, and zing. His journey towards “Pro-Ramesh” was now begun
Moral: Proactive adoption of the four security pillars; security requirements understanding, security awareness, secure design and coding and security testing always keeps your client delighted.