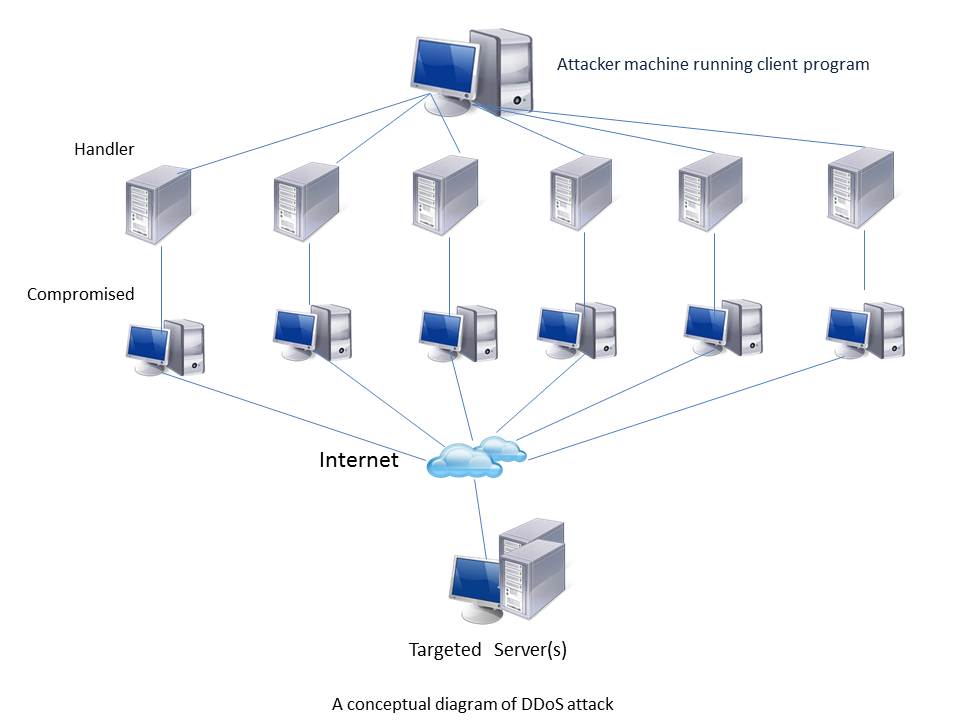
DDoS stands for Distributed denial-of-service or Denial-of-service attack. DDoS attack is an attempt to make machine or network unavailable to its intended users. The attacker sends or implants malware into a file or emails. When the victim downloads or opens the emails, DDoS attacks the computer hardware and others. Under a DDoS attack, hackers send multiple connections continuously to the server. The attack takes place from multiple IP addresses. It takes up the network bandwidth and uses up system resource.
DDoS attacks:
- Direct DDoS attacks (flooding of request packets)
- Reflector DDoS attacks (flooding of response packets)
Direct DDoS attacks (flooding of request packets):
- Attacker sends out packets directly towards the target
- Uses TCP, UDP, ICMP packets and uses random spoofed IP addresses
- Only a few compromised machines are sufficient
Examples:
- TCP SYN flooding; based on TCP three way handshake, the final ACK from source to victim never arrives
- Congesting a victims incoming link using TCP RST packets, ICMP control packets or UDP packets
- TCP (94 %), UDP (2%), ICMP (2%)
Reflector attacks (flooding of response packets):
- Attackers initiate an attack that is relayed to reflector machines, such as routers, web servers etc
- Reflectors may or may not be aware
- In response to requests by attackers, reflectors flood victims with reply packets
- Address of victim spoofed in requests to reflectors
Examples:
- Smurf attacks. ICMP echo packets with spoofed victim addresses are broadcast.
- TCP SYN ACK flooding
- Bandwidth amplification, attack requests that send response packets of much larger size to the victim
Any Type of DDoS attack could be dangerous to the computer no matter which one.
DDoS threat attacks the following services:
- Network Bandwidth
- Server memory
- CPU usage
- Database space
- Database Connection pool
- Application exception handling mechanism
- Hard disk Space
DDoS attacks works in two phases. In the first phase it tries to compromise weak machines in different networks around the world. This phase is called Intrusion phase. It’s in the next phase that they install DDoS tools and start attacking the victim’s machines/site. This phase is called Distributed DDoS attack phase. Attackers use those security holes to compromise the servers in different networks and install the DDoS tools (e.g. Trinoo DDoS tool).
Following things make DDoS attacks simple:
- Vulnerable software /Application running on machine or network
- No monitoring or Data Analysis are being conducted
- Network / machine setup without taking security into account
- Open Network setup
- No Regular Audit /software update being conducted
How to check attack on server:
A quick and useful command for checking if the server is under DDoS:
# netstat -anp|grep tcp|awk ‘{print $5}’| cut -d : -f1|sort|uniq -c|sort –n
It will show the number of connections from all IPs to the server.
To find large number of HTTP processes running use this command:
# ps aux|grep HTTP|wc –l
To find the load just use the command:
# w or uptime
#w 12:00:36 up 1 day, 20:27, 5 users, load average: 0.70, 0.70, 0.57
If you have high load (say 5 or more) and you have large number of HTTP processes then check the following things:
#netstat -lpn|grep :80 |awk '{print $5}'|sort
Check each block of IPs. Let’s assume you have more than 30 connections from a single IP. Under normal cases there is no need for that many number of connection requests from a single IP. Try to identify such IPs/Networks from the list you get.
If more than 5 host/IP connects from the same network then it’s a clear sign of DDoS
Block those IPs/Networks using the following IPTABLES
#iptables -A INPUT -s -j DROP
How to prevent?
There is no perfect solution to avoid DDoS attacks. Prevention is always better than cure. We can prevent it to a certain extent by securing our networks and servers. Firewalls, network, switches and routers are a good way of preventing these attacks. Sometimes the firewalls in computers today cannot stop them but they do stop simple flooding attacks. As a precaution, don’t download anything that doesn’t look real, before you download make sure it is safe.
Prevent your network from being used as a slave, it’s important to note the following things:
- Conduct regular audits on each host on the network to find installed DDoS tools and vulnerable application
- Use tools like Rkdet, Rootkit Hunter, or Chkrootkit to find if a Rootkit has been installed on your system
- Software Vulnerabilities
- Kernel Upgrades and Vulnerabilities
- Check ports
- Check logs
- Check for any Trojans
- Check the system performance
- Check whether backups are maintained
Conclusion
DDoS attacks are a difficult problem. DDoS attacks can be mitigated at the target machine and prevented at the slave network by implementing proper security. Hardware and structural defenses can also be put into place that prevent, or at least potentially minimize, these attacks. Implement monitoring and organizational re‐structuring that can help enable you to quickly identify and respond to an attack. These steps may build your ability to carry on business without interruption.