Following are the considerations for the development and Implementation of software solutions in a PCI-DSS Compliant Environment. These should be treated as functional and/or quality requirements while developing PCI DSS Compliant solution.
- Ensure that all system components and software are protected from known vulnerabilities by having the latest vendor supplied security patches installed. Install critical security patches within one month of release. This applies to all frameworks as well as operating systems and other software installed in production environment.
-
The PCI-DSS requires that access to all systems in the payment processing environment be protected through use of unique users and complex passwords. Unique user accounts indicate that every account used is associated with an individual user with no use of generic group accounts used by more than one user. Additionally any default accounts provided with operating systems, databases and/or devices should be removed/disabled/renamed as soon as possible.
E.g. Default administrator accounts include “administrator” (Windows systems), “sa” (SQL/MSDE), and “root” (UNIX/Linux) should be disabled or removed.
The PCI-DSS standard requires the following password complexity for compliance (often referred to as using “strong passwords”):
a. Passwords must be at least 7 characters
b. Passwords must include both numeric and alphabetic characters
c. Passwords must be changed at least every 90 days
d. New passwords can’t be the same as the last 4 passwords
The PCI-DSS user account requirements beyond uniqueness and password complexity are as follows:
a. If an incorrect password is provided 6 times the account should be locked out
b. Account lock out duration should be at least 30 min. (or until an administrator resets it)
c. Sessions idle for more than 15 minutes should require re-entry of username and password to reactivate the session.
d. Do not use group, shared or generic user accounts
-
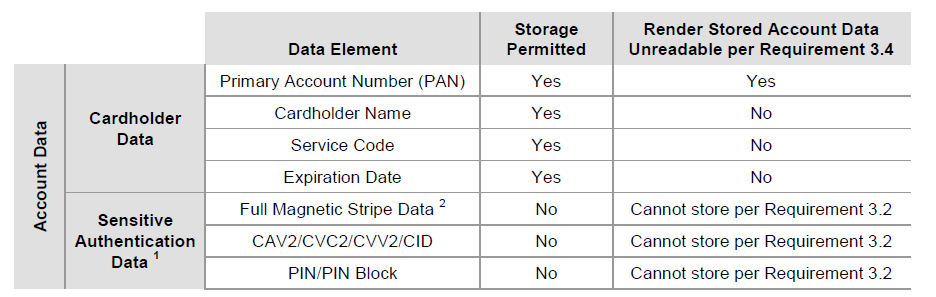
PCI DSS applies wherever account data is stored, processed or transmitted. The primary account number is the defining factor in the applicability of PCI DSS requirements. PCI DSS requirements are applicable if a primary account number (PAN) is stored, processed, or transmitted. If PAN is not stored, processed or transmitted, PCI DSS requirements do not apply.
The following table illustrates commonly used elements of cardholder and sensitive authentication data, whether storage of each data element is permitted or prohibited, and whether each data element must be protected. This table is not exhaustive, but is presented to illustrate the different types of requirements that apply to each data element.
- Removal of custom application accounts, user IDs, and passwords before applications become active or are released to customers.
- Review of custom code prior to release to production or customers in order to identify any potential coding vulnerability.
- There should be separate development/test and production environments.
- Reduce the number of personnel with access to the production environment and cardholder data minimizes risk and helps ensure that access is limited to those individuals with a business need to know.
- Production data (live PANs) are not used for testing or development.
- Test data and accounts should be removed from production code before the application becomes active.